- The Hidden Economy of Blockchain Transaction Ordering
- The Mechanics of MEV: How Value Extraction Actually Works
- Understanding the Transaction Lifecycle
- The Mathematics of Profitable Extraction
- Advanced Extraction Techniques
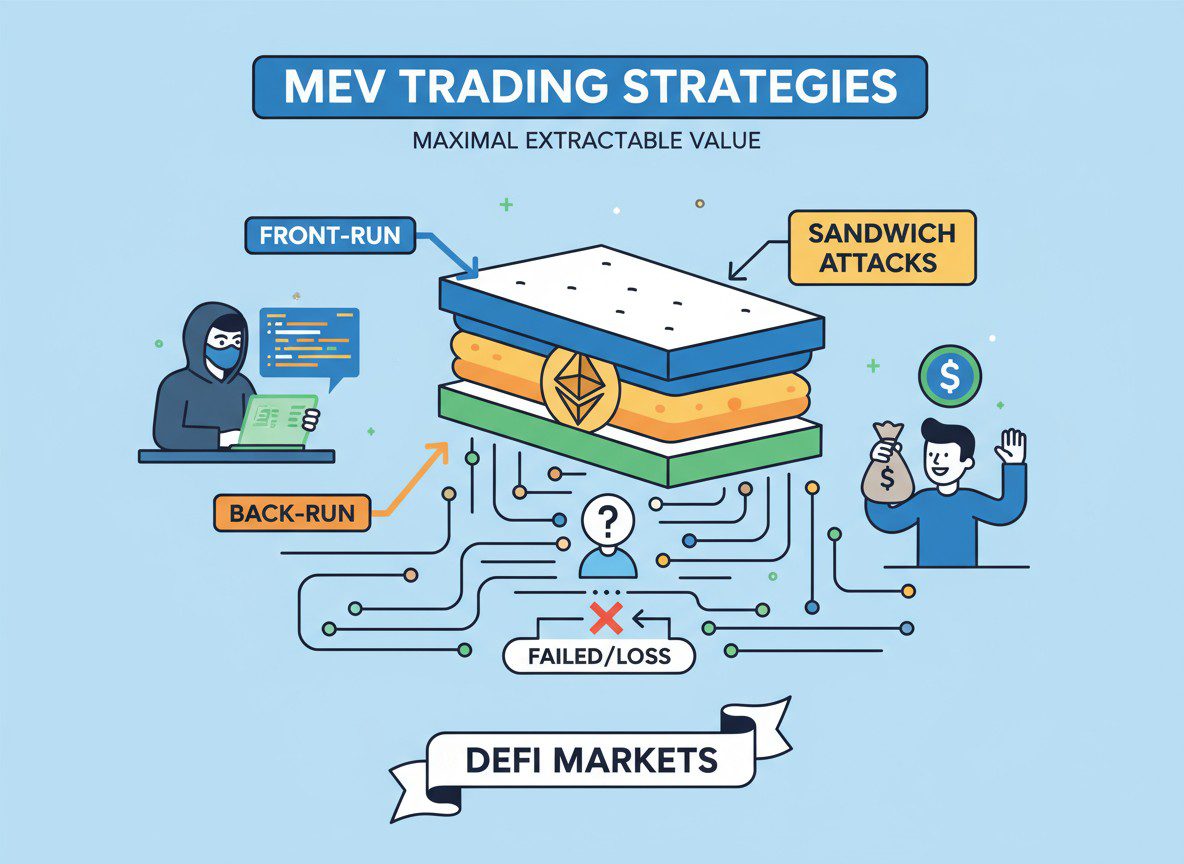
- Sandwich Attacks: The Predatory Side of MEV
- Anatomy of a Sandwich Attack
- Technical Implementation of Sandwich Bots
- Ethical Considerations and Market Impact
- Building Your Own MEV Strategy
- Infrastructure Requirements and Setup
- Strategy Development and Backtesting
- Risk Management and Capital Allocation
- The Evolving MEV Landscape
- MEV in Ethereum’s Post-Merge Era
- Cross-Chain MEV Opportunities
- The Future of MEV: PBS and Beyond
- Protecting Yourself from MEV
- Understanding Your Vulnerability
- Protection Strategies and Tools
- Designing MEV-Resistant Trading Strategies
- Conclusion: Navigating the New Reality of Decentralized Trading
The Hidden Economy of Blockchain Transaction Ordering
Imagine discovering that the very order in which transactions appear in a blockchain block could be worth millions of dollars. This isn’t science fiction—it’s the reality of Maximal Extractable Value (MEV), a phenomenon that has created an entire shadow economy within decentralized finance. Every time you trade on a decentralized exchange like Uniswap or SushiSwap, sophisticated traders might be extracting profit from your transaction through techniques that most users never even know exist.
To understand why MEV represents such a fundamental shift in how we think about trading, consider how traditional financial markets work. When you place an order on the New York Stock Exchange, strict regulations ensure that your order is handled fairly, with price-time priority determining execution order. But in blockchain systems, the rules are different. Miners or validators who create blocks have complete discretion over transaction ordering within certain constraints. This power, combined with the transparency of pending transactions in the mempool, creates extraordinary opportunities for those who understand how to exploit them.
The concept might seem abstract at first, but let me make it concrete with a simple example. Suppose you submit a transaction to buy tokens on a decentralized exchange, and your transaction offers to pay slightly more than the current market price due to slippage tolerance. An MEV trader can see your pending transaction, quickly buy those same tokens just before your transaction executes (pushing the price up), and then sell them to you at your maximum acceptable price. This “sandwich attack” extracts value from your trade without you ever realizing what happened—the blockchain equivalent of someone cutting in line at the store, buying all the items you wanted, and then selling them to you at a markup.
The MEV ecosystem has evolved from simple arbitrage opportunities to complex strategies involving flash loans, multi-block extraction, and even coordinated attacks across multiple protocols. Understanding these mechanisms isn’t just academic curiosity—it’s becoming essential for anyone serious about DeFi trading, as MEV extraction can significantly impact your trading costs and strategy effectiveness.
The Mechanics of MEV: How Value Extraction Actually Works
Understanding the Transaction Lifecycle
To grasp how MEV extraction works, we need to follow a transaction’s journey from creation to inclusion in a block. When you initiate a transaction on Ethereum or any other blockchain, it doesn’t immediately get recorded. Instead, it enters a waiting room called the mempool (memory pool), where it sits alongside thousands of other pending transactions, all visible to anyone who knows where to look.
Think of the mempool as a transparent waiting room where everyone can see what others are planning to do. If you walk into this room holding a sign that says “I want to buy 100 ETH worth of tokens at any price up to 5% above market,” sophisticated traders immediately start calculating whether they can profit from your intended purchase. This transparency, which is fundamental to blockchain’s trustless nature, creates the very opportunities that MEV traders exploit.
The selection and ordering of transactions from the mempool into blocks traditionally followed simple rules—miners would include transactions paying the highest gas fees first, maximizing their revenue. But as DeFi grew and transaction values increased, miners realized that the power to order transactions was worth far more than just gas fees. They could extract additional value by strategically ordering transactions or even inserting their own transactions at advantageous positions.
Table 1: MEV Opportunity Types and Characteristics
| MEV Type | Complexity | Typical Profit | Risk Level | Competition | Required Capital |
|---|---|---|---|---|---|
| DEX Arbitrage | Low | $10-1,000 per tx | Low | High | Moderate |
| Sandwich Attacks | Medium | $50-5,000 per tx | Medium | High | Low-Moderate |
| Liquidations | Medium | $500-50,000 per tx | Medium | Moderate | High |
| Cross-DEX Arbitrage | High | $100-10,000 per tx | Low | Moderate | Moderate |
| Multi-Block MEV | Very High | $1,000-100,000 | High | Low | Very High |
| Flash Loan Attacks | Extreme | $10,000-1M+ | Very High | Very Low | None (borrowed) |
The introduction of Ethereum’s EIP-1559 and the transition to Proof of Stake changed some dynamics but didn’t eliminate MEV. Instead of miners, validators now control transaction ordering. And with the emergence of MEV-Boost and other infrastructure, the extraction process has become more systematic and democratized, though still favoring those with technical sophistication.
The Mathematics of Profitable Extraction
Let me walk you through the mathematical framework that MEV bots use to identify profitable opportunities. The core calculation involves comparing the expected profit from extraction against the costs of execution, including gas fees, capital requirements, and competition from other bots. This might seem straightforward, but the reality involves sophisticated modeling of multiple uncertain variables.
Consider a simple arbitrage opportunity between two DEXs. If Token A trades at price P₁ on Uniswap and P₂ on SushiSwap, where P₂ > P₁, the gross profit from buying on Uniswap and selling on SushiSwap equals (P₂ – P₁) × Q, where Q is the quantity traded. But this simple calculation ignores several crucial factors that determine actual profitability.
First, we must account for price impact. Large trades move prices according to the automated market maker (AMM) formula. For constant product AMMs like Uniswap V2, the price impact can be calculated using the formula:
Price Impact = (x × y) / (x + Δx) – y + Δy
Where x and y are the reserve balances and Δx and Δy are the trade amounts. This non-linear relationship means that larger trades face increasingly worse prices, creating an optimization problem to find the ideal trade size.
Second, gas costs must be carefully modeled. A typical MEV transaction might consume 200,000-500,000 gas units, and during competitive periods, gas prices can spike to hundreds of gwei. The profitability calculation becomes:
Net Profit = Gross Profit – (Gas Used × Gas Price × ETH Price) – Protocol Fees
This creates a threshold effect where opportunities below a certain value aren’t worth pursuing, and competition for larger opportunities drives up gas prices until profits are competed away.
Advanced Extraction Techniques
Modern MEV extraction has evolved far beyond simple arbitrage. Sophisticated strategies now involve multiple steps, complex state analysis, and even game-theoretic considerations about competitor behavior. Understanding these advanced techniques reveals the true depth of the MEV ecosystem and why it represents such a fundamental challenge to fair and efficient markets.
Flash loan-enabled strategies represent one of the most powerful tools in an MEV extractor’s arsenal. By borrowing large amounts of capital for a single transaction, traders can exploit opportunities that would otherwise require millions in capital. For instance, a trader might borrow 10,000 ETH, use it to manipulate prices across multiple DEXs, extract profit from the price discrepancies they created, and repay the loan—all within a single atomic transaction that either completes entirely or fails with no cost except gas.
Cross-protocol strategies add another layer of sophistication. These involve interactions between multiple DeFi protocols to extract value that wouldn’t be available from any single protocol. A classic example involves borrowing from Aave, swapping on Curve, providing liquidity to Balancer, and then unwinding all positions for a profit. The complexity of these strategies makes them difficult to detect and compete against, providing sustainable advantages to teams with the technical capability to implement them.
Sandwich Attacks: The Predatory Side of MEV
Anatomy of a Sandwich Attack
Sandwich attacks represent the most controversial form of MEV extraction because they directly extract value from other traders’ transactions. To understand how these attacks work, imagine you’re at an auction where you can see everyone’s maximum bid before the auction starts, and you have the ability to place your own bids immediately before and after any other bidder. This is essentially the power that sandwich attackers wield in DeFi markets.
The attack unfolds in three precise steps that must execute in exact sequence. First, the attacker identifies a target transaction in the mempool—typically a large trade with significant slippage tolerance. Second, they place a buy order just before the victim’s transaction, purchasing the asset the victim wants and driving up its price. Third, they place a sell order immediately after the victim’s transaction, selling the asset back to the market at a profit. The victim’s transaction gets “sandwiched” between these two trades, hence the name.
Let me illustrate with specific numbers to make this crystal clear. Suppose you want to swap 10 ETH for USDC on Uniswap, and you set a 1% slippage tolerance (common for large trades). The current price might give you 35,000 USDC, but you’re willing to accept as little as 34,650 USDC. A sandwich attacker sees your pending transaction and quickly buys USDC with their own ETH, pushing the price up so that your 10 ETH only gets you 34,650 USDC—your minimum acceptable amount. They then sell their USDC right after your trade executes, profiting from both the price impact of your trade and the difference between what you could have received and what you actually received.
Table 2: Sandwich Attack Profitability Analysis
| Victim Trade Size | Slippage Setting | Attacker Capital | Expected Profit | Success Rate | Gas Cost |
|---|---|---|---|---|---|
| $1,000-5,000 | 0.5% | $500-2,000 | $5-25 | 60-70% | $50-100 |
| $5,000-20,000 | 1.0% | $2,000-10,000 | $50-200 | 70-80% | $75-150 |
| $20,000-100,000 | 1.5% | $10,000-50,000 | $300-1,500 | 80-85% | $100-300 |
| $100,000+ | 2.0% | $50,000+ | $2,000+ | 85-90% | $200-1000 |
The profitability of sandwich attacks depends on several factors that create a complex optimization problem. The attacker must balance the size of their frontrun transaction (larger means more profit but higher capital requirements and risk), the gas price they’re willing to pay (higher ensures inclusion but reduces profit), and the competition from other sandwich bots targeting the same transaction.
Technical Implementation of Sandwich Bots
Building a sandwich bot requires sophisticated technical infrastructure that can identify opportunities, calculate profitability, and execute attacks faster than competitors. The technical stack typically involves several interconnected components working in perfect synchronization, as even milliseconds of delay can mean the difference between profit and loss.
The monitoring system forms the foundation of any sandwich bot. This component maintains connections to multiple Ethereum nodes, subscribing to pending transaction pools and filtering for potential targets. The system must parse transaction data in real-time, decode function calls to identify swaps, and extract parameters like token addresses, amounts, and slippage settings. This requires deep knowledge of smart contract ABIs and efficient parsing algorithms that can process thousands of transactions per second.
Once a potential target is identified, the simulation engine takes over. This component uses tools like Hardhat or custom EVM implementations to simulate the sandwich attack locally, calculating exact profit amounts and checking for potential failures. The simulation must account for complex factors like multi-hop swaps, protocol fees, and potential interference from other MEV bots. Modern systems use optimistic simulation, assuming successful execution and only checking for obvious failures to minimize latency.
The execution engine represents the most critical component, responsible for crafting and submitting the sandwich transactions with precise timing and gas pricing. This often involves using flashbots bundles or private mempools to ensure atomic execution—either all three transactions execute in order, or none execute at all. The engine must dynamically adjust gas prices based on competition and opportunity value, sometimes paying thousands of dollars in gas fees for particularly profitable sandwiches.
Ethical Considerations and Market Impact
The prevalence of sandwich attacks raises fundamental questions about fairness and efficiency in decentralized markets. While some argue that MEV extraction is simply the natural result of market mechanics and that traders who don’t want to be sandwiched should use private mempools or MEV protection services, others contend that sandwich attacks constitute a form of front-running that would be illegal in traditional financial markets.
The market impact extends beyond individual trades. Research suggests that sandwich attacks increase overall trading costs by 0.1-0.3% on average, with certain trading pairs experiencing much higher implicit costs. This “MEV tax” particularly affects retail traders who lack access to sophisticated protection mechanisms, potentially undermining DeFi’s promise of democratized finance. Large trades face a difficult choice: accept sandwich attacks as a cost of doing business, split trades into smaller pieces (increasing gas costs), or use private order flow channels that may compromise decentralization.
The ecosystem has responded with various protection mechanisms. Flashbots Protect offers a free RPC endpoint that routes transactions through private mempools, preventing them from being seen by sandwich bots. Some DEXs have implemented commit-reveal schemes or time-weighted average price (TWAP) orders that make sandwiching unprofitable. However, these solutions often involve trade-offs between protection, cost, and execution speed.
Building Your Own MEV Strategy
Infrastructure Requirements and Setup
Developing a successful MEV strategy requires significant technical infrastructure that goes well beyond simple trading bots. The entire system must operate with extremely low latency, high reliability, and sophisticated risk management. Understanding these requirements helps explain why MEV extraction tends to be dominated by well-funded teams rather than individual traders.
The foundation starts with node infrastructure. Running your own Ethereum nodes provides the fastest access to mempool data and reduces dependence on third-party services. A competitive setup might include multiple geographically distributed nodes, each running on dedicated hardware with NVMe SSDs and high-bandwidth connections. Some teams colocate servers in the same data centers as major mining pools or validators to minimize network latency. The monthly cost for this infrastructure can easily exceed $10,000 for a serious operation.
Table 3: MEV Infrastructure Components and Costs
| Component | Basic Setup | Professional Setup | Enterprise Setup | Key Considerations |
|---|---|---|---|---|
| Node Infrastructure | $200/month (Infura/Alchemy) | $2,000/month (Dedicated nodes) | $10,000+/month (Colocated) | Latency, reliability |
| Monitoring System | Python scripts | Go/Rust service | Custom FPGA solution | Processing speed |
| Simulation Engine | Ganache/Hardhat | Custom EVM | Parallel simulation | Accuracy vs speed |
| Execution System | Web3.py/Ethers.js | Flashbots/Eden | Private orderflow | Success rate |
| Risk Management | Manual limits | Automated controls | ML-based system | Loss prevention |
| Development Time | 200-400 hours | 1000-2000 hours | 5000+ hours | Opportunity cost |
Beyond hardware, the software stack requires expertise across multiple domains. Smart contract development skills are essential for understanding protocol mechanics and implementing on-chain components. Systems programming in languages like Rust or Go becomes necessary for building low-latency components. Data engineering expertise helps in storing and analyzing the massive amounts of historical data needed for strategy optimization. And increasingly, machine learning knowledge provides competitive advantages in prediction and optimization tasks.
Strategy Development and Backtesting
Developing profitable MEV strategies requires a systematic approach that combines market insight, technical capability, and rigorous testing. The process typically begins with opportunity identification—analyzing historical blockchain data to find patterns of extractable value that aren’t already heavily competed. This might involve studying new protocols for vulnerabilities, identifying inefficiencies in cross-protocol interactions, or discovering statistical patterns that predict profitable opportunities.
The backtesting process for MEV strategies differs significantly from traditional trading backtests. You’re not just simulating trades; you’re simulating an entire competitive environment where multiple actors compete for the same opportunities. This requires modeling competitor behavior, gas price dynamics, and the probabilistic nature of transaction inclusion. A proper backtest might replay historical blocks while simulating what would happen if your bot had competed for various opportunities, accounting for how your actions would have affected gas prices and competitor responses.
Consider the complexity of backtesting a sandwich strategy. You need to identify all historical transactions that could have been sandwiched, calculate the optimal sandwich parameters for each, simulate the gas auction that would have occurred with competitors, and determine whether your bot would have won the opportunity at a profitable gas price. This process requires processing terabytes of historical data and running millions of simulations, often taking days or weeks for comprehensive testing.
Risk Management and Capital Allocation
MEV strategies involve unique risks that require sophisticated management approaches. Unlike traditional trading where risks are primarily market-based, MEV extraction faces technical risks (smart contract bugs, network issues), competitive risks (being outbid or attacked by other bots), and regulatory risks (potential legal challenges to certain extraction methods). A comprehensive risk framework must address all these dimensions while maintaining profitability.
Capital allocation in MEV strategies follows different principles than traditional portfolio management. Rather than diversifying across assets, you’re diversifying across opportunity types and extraction methods. A balanced MEV operation might allocate 30% of capital to low-risk arbitrage, 40% to medium-risk sandwiching, 20% to high-risk liquidations, and keep 10% as reserve for unexpected opportunities. This allocation must be dynamic, adjusting based on market conditions and competition levels.
The use of flash loans adds another dimension to capital management. While flash loans eliminate capital requirements for certain strategies, they introduce execution risk—if any part of the transaction fails, the entire sequence reverts. Sophisticated strategies might combine owned capital with flash loans, using proprietary funds for high-certainty opportunities while leveraging flash loans for larger but riskier extractions. This hybrid approach optimizes capital efficiency while maintaining operational flexibility.
The Evolving MEV Landscape
MEV in Ethereum’s Post-Merge Era
Ethereum’s transition to Proof of Stake fundamentally altered the MEV landscape, creating new opportunities and challenges for extractors. Instead of miners competing through hash power, validators now propose blocks on a scheduled basis, changing the dynamics of MEV extraction. The introduction of MEV-Boost created a marketplace where validators can outsource block building to specialized entities, leading to the emergence of professional block builders who optimize transaction ordering across entire blocks.
This new architecture has led to the concentration of block building among a small number of sophisticated actors. These builders compete to create the most valuable blocks, bidding for the right to have their blocks proposed by validators. The competition drives efficiency but raises concerns about centralization and censorship resistance. Understanding these dynamics becomes crucial for anyone operating in the MEV space, as the relationship with builders often determines extraction success.
The post-merge era has also seen the emergence of multi-block MEV, where strategies span multiple consecutive blocks. Validators who know they’ll propose multiple blocks in sequence can execute strategies impossible for single-block extractors. This might involve manipulating protocol parameters in one block to create opportunities in the next, or gradually accumulating positions across blocks before executing a profitable exit. While still rare, these strategies represent the cutting edge of MEV extraction and likely preview future developments.
Cross-Chain MEV Opportunities
As blockchain ecosystems become increasingly interconnected through bridges and cross-chain protocols, MEV opportunities are expanding beyond single chains. Cross-chain MEV involves extracting value from price discrepancies, liquidity imbalances, or protocol interactions across different blockchains. This emerging field requires infrastructure and expertise spanning multiple ecosystems, each with its own technical characteristics and MEV dynamics.
Table 4: Cross-Chain MEV Characteristics by Ecosystem
| Blockchain | Block Time | MEV Infrastructure | Main Opportunities | Technical Challenges |
|---|---|---|---|---|
| Ethereum | ~12 seconds | Highly developed | All types | High competition |
| BSC | ~3 seconds | Moderate | Arbitrage, Sandwiches | Centralization |
| Polygon | ~2 seconds | Developing | Arbitrage, Liquidations | Reorg risk |
| Arbitrum | ~0.25 seconds | Emerging | Cross-chain arb | Sequencer control |
| Solana | ~0.4 seconds | Limited | High-frequency arb | Different architecture |
| Avalanche | ~2 seconds | Basic | Cross-chain opportunities | Multiple subnets |
Consider a typical cross-chain arbitrage scenario. Token prices on Ethereum’s Uniswap might diverge from prices on Polygon’s QuickSwap due to different user bases and liquidity depths. An MEV extractor could buy tokens on the cheaper chain, bridge them to the expensive chain, and sell for profit. But this simple description hides enormous complexity—the extractor must account for bridge fees and delays, gas costs on both chains, price impact on both DEXs, and the risk that prices converge before the bridge transfer completes.
The technical implementation of cross-chain MEV requires maintaining infrastructure across multiple blockchains, understanding different consensus mechanisms and finality guarantees, and managing complex asynchronous operations. Some teams use specialized prediction models to forecast price movements during bridge delays, while others focus on atomic cross-chain swaps that eliminate timing risk but require more sophisticated smart contract interactions.
The Future of MEV: PBS and Beyond
The future of MEV extraction is being shaped by Proposer-Builder Separation (PBS), a protocol change that formally separates the roles of block proposing and block building. This architectural shift, planned for future Ethereum upgrades, aims to address centralization concerns while preserving the efficiency gains from specialized block building. Understanding PBS becomes essential for long-term MEV strategy development.
Under PBS, validators auction their block proposal rights to builders through an in-protocol mechanism, replacing the current out-of-protocol MEV-Boost system. This creates a more transparent and fair marketplace for MEV extraction while potentially redistributing value from builders to validators and ultimately to ETH stakers. For MEV extractors, this means adapting strategies to work within a more regulated and competitive environment where extraction opportunities might be more evenly distributed.
Looking further ahead, developments like threshold encryption for mempool transactions could fundamentally alter MEV dynamics. If transactions remain encrypted until after ordering is determined, sandwich attacks become impossible while some forms of arbitrage remain viable. This would shift the MEV landscape toward strategies that don’t depend on seeing transaction contents in advance, favoring statistical arbitrage and protocol-specific opportunities over predatory extraction.
Protecting Yourself from MEV
Understanding Your Vulnerability
As a trader in DeFi markets, understanding your vulnerability to MEV extraction helps you make informed decisions about protection strategies. Not all trades face equal MEV risk—small swaps of liquid tokens might lose only a few dollars to MEV, while large trades of illiquid tokens could lose thousands. Learning to assess your MEV exposure allows you to balance protection costs against potential losses.
Your vulnerability depends on several factors that you can often control or influence. Trade size obviously matters—larger trades create bigger opportunities for extractors. But equally important is your slippage tolerance setting. That seemingly innocent 1% slippage you set “just to be safe” is actually announcing to MEV bots exactly how much value they can extract from your trade. Token selection also matters significantly; trading well-established pairs like ETH/USDC faces less MEV risk than trading newly launched tokens with thin liquidity.
The timing and method of transaction submission create another vulnerability vector. Transactions submitted during high-activity periods face more competition from MEV bots, while those submitted during quiet periods might sit in the mempool longer, giving extractors more time to identify opportunities. The RPC endpoint you use determines whether your transaction enters the public mempool (visible to MEV bots) or goes through private channels that offer protection.
Protection Strategies and Tools
The ecosystem has developed various tools and strategies to protect users from MEV extraction, each with different trade-offs between protection level, cost, and convenience. Understanding these options helps you choose appropriate protection for your specific needs rather than blindly accepting MEV losses or overpaying for unnecessary protection.
Table 5: MEV Protection Methods Comparison
| Protection Method | Effectiveness | Cost | Complexity | Best Use Case |
|---|---|---|---|---|
| Flashbots Protect RPC | High | Free | Very Low | General trading |
| Private Mempools | Very High | Variable fees | Low | Large trades |
| Cowswap/0x | High | 0.1-0.3% fee | Low | Token swaps |
| Commit-Reveal Schemes | Very High | Gas overhead | Medium | Sensitive operations |
| Time-Weighted Orders | Medium | Time delay | Low | Non-urgent trades |
| MEV Blocker | High | Free | Very Low | Casual users |
The simplest protection involves using Flashbots Protect or similar private mempool services. By configuring your wallet to use these RPC endpoints, your transactions bypass the public mempool entirely, making them invisible to MEV bots. The trade-off is slightly slower inclusion times and dependency on centralized infrastructure, but for most users, these downsides are negligible compared to MEV protection benefits.
For more sophisticated needs, intent-based protocols like CoWSwap or 0x offer professional-grade execution that inherently resists MEV. These protocols use batch auctions or request-for-quote systems that make sandwich attacks unprofitable or impossible. While they charge fees, these costs are often offset by better execution prices and MEV protection, particularly for large trades.
Designing MEV-Resistant Trading Strategies
Beyond using protection tools, you can design your trading strategies to naturally resist MEV extraction. This involves understanding how MEV bots identify targets and structuring your trades to be unprofitable or impossible to exploit. These techniques require more thought and planning but can significantly reduce your MEV exposure without relying on external protection services.
One effective approach involves breaking large trades into smaller chunks executed over time. Instead of swapping 100 ETH in a single transaction, you might execute 10 trades of 10 ETH each, spread across several blocks. While this increases gas costs, it reduces the profitability of sandwich attacks and makes your trades less attractive targets. Automated tools can handle this splitting programmatically, optimizing chunk sizes based on current gas prices and MEV activity levels.
Another strategy leverages limit orders instead of market swaps. By placing limit orders on order book DEXs or using protocols with limit order functionality, you specify exactly what price you’re willing to accept, eliminating slippage-based MEV extraction. The trade-off is potentially slower execution and the need to actively manage orders, but for non-urgent trades, this approach offers strong MEV resistance with minimal additional cost.
Conclusion: Navigating the New Reality of Decentralized Trading
The emergence of MEV has fundamentally transformed the landscape of decentralized trading, creating a parallel economy where the order of transactions becomes as important as their content. What started as simple arbitrage opportunities has evolved into a sophisticated ecosystem of extraction strategies, protection mechanisms, and infrastructure providers, all competing for value that was previously invisible or inaccessible. Understanding this hidden layer of blockchain economics is no longer optional for serious DeFi participants—it’s essential for both protecting yourself from extraction and potentially participating in this new form of value capture.
The technical and ethical complexities of MEV reflect broader challenges in decentralized systems. How do we balance the transparency that enables trustless interaction with the privacy needed for fair markets? Can we preserve decentralization while acknowledging that sophisticated actors will always have advantages? These questions don’t have easy answers, but engaging with them thoughtfully helps us build better systems and make more informed decisions as market participants.
For traders looking to protect themselves, the key message is awareness and appropriate protection. Not every trade needs maximum MEV protection—sometimes the cure is worse than the disease. But understanding your vulnerability and available protection options allows you to make informed decisions rather than unknowingly subsidizing MEV extractors. Start with simple protections like Flashbots Protect for everyday trading, and graduate to more sophisticated solutions as your trading volume and complexity increase.
For those interested in MEV extraction itself, remember that this is not a casual endeavor. Successful MEV extraction requires significant technical expertise, capital investment, and risk tolerance. The competition is fierce, with well-funded teams using cutting-edge technology to compete for the same opportunities. But for those with the necessary skills and resources, MEV represents one of the most intellectually challenging and potentially profitable areas in all of cryptocurrency trading.
As we look toward the future, MEV will likely become more institutionalized and regulated, with clearer rules about acceptable extraction methods and required protections for users. The infrastructure will continue evolving, potentially making some current strategies obsolete while creating entirely new categories of opportunity. What remains constant is that understanding MEV—whether as a trader seeking protection or an extractor seeking profit—provides a crucial edge in navigating the complex and rapidly evolving world of decentralized finance. The traders who thrive will be those who understand not just what appears on the surface of these markets, but also the hidden currents that flow beneath.